Every day, credit card machines facilitate seamless transactions with a simple tap, insert, or swipe. These devices may appear like magic, but have you ever looked into the inner workings behind these devices? We invite you to embark on a journey to understand the process and functionality behind credit card machines.
What is a credit card machine?
A credit card machine, also known as a point-of-sale (POS) terminal, card reader, payment terminal, or credit card terminal, is a device used by businesses to facilitate electronic payments made with credit and debit cards. These machines are designed to read the data stored on the magnetic stripe or EMV chip of a card and securely process transactions.
You will hear the term EMV a lot in payments. EMV stands for “Europay, Mastercard, and Visa”, the three companies that created the standard. It is basically a security standard that all payment companies use.

Credit card machines play a crucial role in modern commerce by allowing customers to make purchases, and they are used in various settings, including retail stores, restaurants, and other transaction situations. Credit card machines offer features for authorization, payment processing, and transaction management, ensuring the secure and efficient transfer of funds between customers and businesses.
Main functions of a credit card machine
Credit card machines serve as the backbone of payment processing for businesses of all sizes. These devices enable the smooth execution of sales transactions, captures essential transaction data, and empowers businesses to manage the complexities of refunds, voids, and daily settlement. Here are some of the key functions that credit card machines enable.
Sales Transaction: The primary function of a credit card machine is to facilitate the sale of goods or services. It processes the transaction when a customer makes a payment using their credit or debit card. The machine communicates with the cardholder’s bank (the issuing bank) to authorize and complete the purchase.
Authorization and Capture: The credit card machine can authorize a transaction, but not actually process it. It would process the transaction at a later date with the “capture” functionality. Authorization basically sends an authorization request to the issuing bank to verify the card’s validity and check if the cardholder has sufficient funds or credit available. This is commonly used when you check in at hotels. They authorize something like $250 to verify your credit card.
Payment Confirmation: Once the issuing bank approves the transaction, the credit card machine generates a payment confirmation, indicating that the sale has been authorized. The customer typically receives a receipt for their records.
Refunds: Credit card machines have the capability to process refunds. If a customer returns a product or requests a refund for a service, the machine can initiate a refund transaction, crediting the amount back to the cardholder’s account. This helps businesses manage returns and maintain customer satisfaction.
Void Transactions: In cases where a sale needs to be canceled before it is settled, the credit card machine can void the transaction. This function ensures that the customer is not charged, and the authorization is canceled.
Batch Settlement: At the end of the business day, the credit card machine performs a batch settlement. It totals all the authorized transactions and initiates the process of depositing the funds into the merchant’s bank account. This is an essential step for reconciling daily sales.
Reporting: Credit card machines offer reporting capabilities to provide businesses with insights into their transactions. These reports can include sales summaries, transaction history, and other data to help with accounting and record-keeping.
Offline Mode: In situations where the internet connection is temporarily unavailable, credit card machines might have an offline mode. This mode allows them to continue processing transactions and store them locally until connectivity is restored.
Transaction History: Credit card machines maintain a transaction history, which is important for record-keeping and dispute resolution. This history includes details of all authorized transactions, including sales, refunds, and voids.
Step by step transaction process
Credit card machine processing involves three pivotal stages: authorization, capture, and settlement. Each of these stages plays a crucial role in the payment journey:
Step 1: Authorization
- Card Entry: The customer inserts, swipes, or taps their credit or debit card into the card reader of the credit card machine.
- Data Transmission: The credit card machine reads the data from the card’s magnetic stripe or EMV chip.
- Authorization Request: The machine sends an authorization request to the issuing bank (the bank that issued the customer’s credit or debit card). This request includes transaction details like the amount and card information.
- Bank Verification: The issuing bank verifies the transaction by checking the cardholder’s account for available credit or funds and performs security checks to prevent fraud.
- Authorization Response: The issuing bank sends an authorization response to the credit card machine. If approved, this response includes an authorization code.
Step 2: Capture
- Transaction Data Storage: While authorization verifies the transaction, the actual funds transfer or capture happens later. The credit card machine stores the authorized transaction data for later processing.
Step 3: Settlement
- Batching: At the end of the day or another predetermined time, the credit card machine batches together all the authorized transactions.
- Funds Transfer: The batch of authorized transactions is sent to the credit card company or payment processor for settlement. The funds are transferred from the customer’s bank to the merchant’s account.
Step 4: Payment Confirmation
- Receipt: The credit card machine generates a payment confirmation and issues a receipt for the customer’s records. The receipt typically includes transaction details and the authorization code.
Step 5: Refunds and Void Transactions
- Refunds: If a customer returns a product or requests a refund, the credit card machine can initiate a refund transaction. The refunded amount is credited back to the cardholder’s account.
- Void Transactions: In cases where a sale needs to be canceled before it is settled, the credit card machine can void the transaction, ensuring the customer is not charged.
Behind the scenes process of a merchant account
Every credit card machine needs a merchant account set up for it to work. Behind the scenes of a transaction, there are numerous players involved, described in the chart below like the cardholder’s bank, Visa, and the payment processor. The merchant account serves as a financial intermediary, allowing businesses to accept various payment methods such as credit cards or mobile payments.
This enables the smooth transfer of funds from the customer’s account to the merchant’s account, ensuring a secure and efficient transaction process.
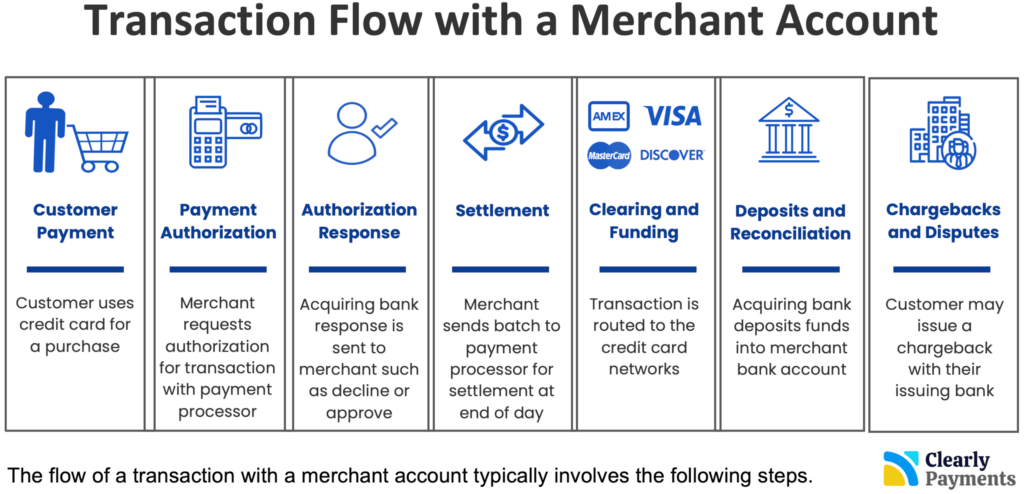
It’s important to note that the specific flow and timelines can vary depending on the payment processor, acquiring bank, and the merchant’s agreement with their service providers. Additionally, online transactions may involve additional security measures, such as 3D Secure authentication, to mitigate fraud risks.
How EMV chip card readers work
EMV, a global standard under the guardianship of industry giants such as American Express, Discover, JCB, Mastercard, UnionPay, and Visa, represents the zenith of chip card technology. While Australia transitioned to EMV back in 2013, some regions, notably the United States, are still in the throes of the shift from magstripe to chip technology.
Chip cards are celebrated for their robust security. The dynamic encryption of data on these cards presents a formidable barrier to fraudsters attempting to access and misuse cardholder information. Notably, EMV technology has succeeded in substantially reducing global fraud rates. Early adopters who abandoned magstripe cards in favor of EMV technology reported significant declines in fraudulent activities. You can read more about fraud statistics.
Equipped with an embedded computer chip housing bank details, EMV cards boast ever-changing payment information. When inserted into a reader, a complex, encrypted conversation occurs, culminating in the generation of a unique code with each insertion. This data is then securely transmitted to the acquiring bank, shielding the transaction from potential threats.
How contactless card readers work
Contactless (NFC) payments are renowned for their speed and efficiency, making them ideal for bustling checkout scenarios. These transactions, while rapid, maintain the same level of security as chip cards, underpinned by encryption and dynamic data.
NFC, often referred to as “contactless” or “tap-and-go” payments, leverages “near field communication” technology. Similar to chip cards, NFC data undergoes encryption and dynamic modification, ensuring that each transaction carries unique data. Prominent examples of NFC payments include contactless cards and mobile wallets like Apple Pay, Android Pay, and Samsung Pay.
For NFC payments, customers simply tap their cards or place their mobile wallet-enabled devices, such as smartphones, over the credit card machine, initiating lightning-fast transactions.
With tap-and-go cards, the transaction process closely resembles that of EMV transactions. However, when using mobile wallets like Apple Pay, an additional layer of security emerges. Apple Pay employs a technology known as tokenization, safeguarding banking information. During setup, a photograph of the credit card is captured within the Apple Pay app. Apple then exchanges this information with a “token,” which is transmitted to the phone. This unique token does not contain the actual credit card details, rendering them inaccessible to fraudsters. Moreover, a distinct token is generated for each transaction, providing an extra layer of protection.
How magnetic stripe (magstripe) readers work
Magstripe card readers, also known as magnetic stripe card readers, are devices designed to read the data stored on the magnetic stripe of credit, debit, or identification cards. These magnetic stripes are typically found on the back of these cards and contain important information about the cardholder’s account.
The data on the magnetic stripe is stored using magnetic particles. This stripe consists of three tracks, each containing different types of information. Track 1 is typically used for the cardholder’s name and account number, Track 2 contains the primary account number (PAN), and Track 3, which is less common, stores additional data.
Although magstripe card readers have been widely used for decades, they are being phased out in favor of more secure technologies, such as EMV chip cards and contactless payments (e.g., NFC technology). These newer technologies offer enhanced security features and help reduce the risk of card skimming and fraud associated with magstripe cards.




